I am pleased to announce a new Citizen Lab report, authored by Bill Marczak, John Scott-Railton, Sarah McKune, Bahr Abdul Razzak, and myself, entitled “Hide and Seek: Tracking NSO Group’s Pegasus Spyware to Operations in 45 Countries.” This report is the latest in a major research area for the Citizen Lab: the proliferation and abuse of commercial spyware.
Commercial spyware is sophisticated surveillance technology sold by companies to governments under the justification of assisting in law enforcement or national security investigations. It typically tricks targets into clicking on links or attachments and then takes advantage of undisclosed and often very valuable software flaws to surreptitiously take control of a target’s device. Once in control, an operator can secretly monitor emails and chats, even those that are protected with encryption, track movements and locations, and record audio and video.
As numerous government agencies have both the resources and a growing appetite for surveillance capabilities, the market for commercial spyware is lucrative and expanding. The company at the centre of our latest report, Israel-based NSO Group, was recently valued at around USD 1 billion.
Naturally, this market is also highly secretive. Spy agencies and the companies that service them do not, as a matter of practice, publicly disclose their contracts or operations. However, even the most sophisticated surveillance operations leave digital traces in the open that careful researchers can discover. One aim of our research is to shed light on what is otherwise opaque principally through structured, peer-reviewed Internet scanning techniques and other technical means we have refined.
The research for our latest report was led once again by Citizen Lab senior fellow Bill Marczak. From August 2016 to August 2018, we scanned the entire Internet on a regular basis for servers associated with NSO Group’s “Pegasus” spyware designed to target iPhones, and found 1,091 IP addresses that matched our fingerprint and 1,014 domain names that pointed to them. Using a novel technique we call Athena as well as a newly designed global DNS Cache Probing method, we were able to identify a total of 45 countries where Pegasus operators (which we group into more than 30 likely government clients) may be conducting surveillance operations.
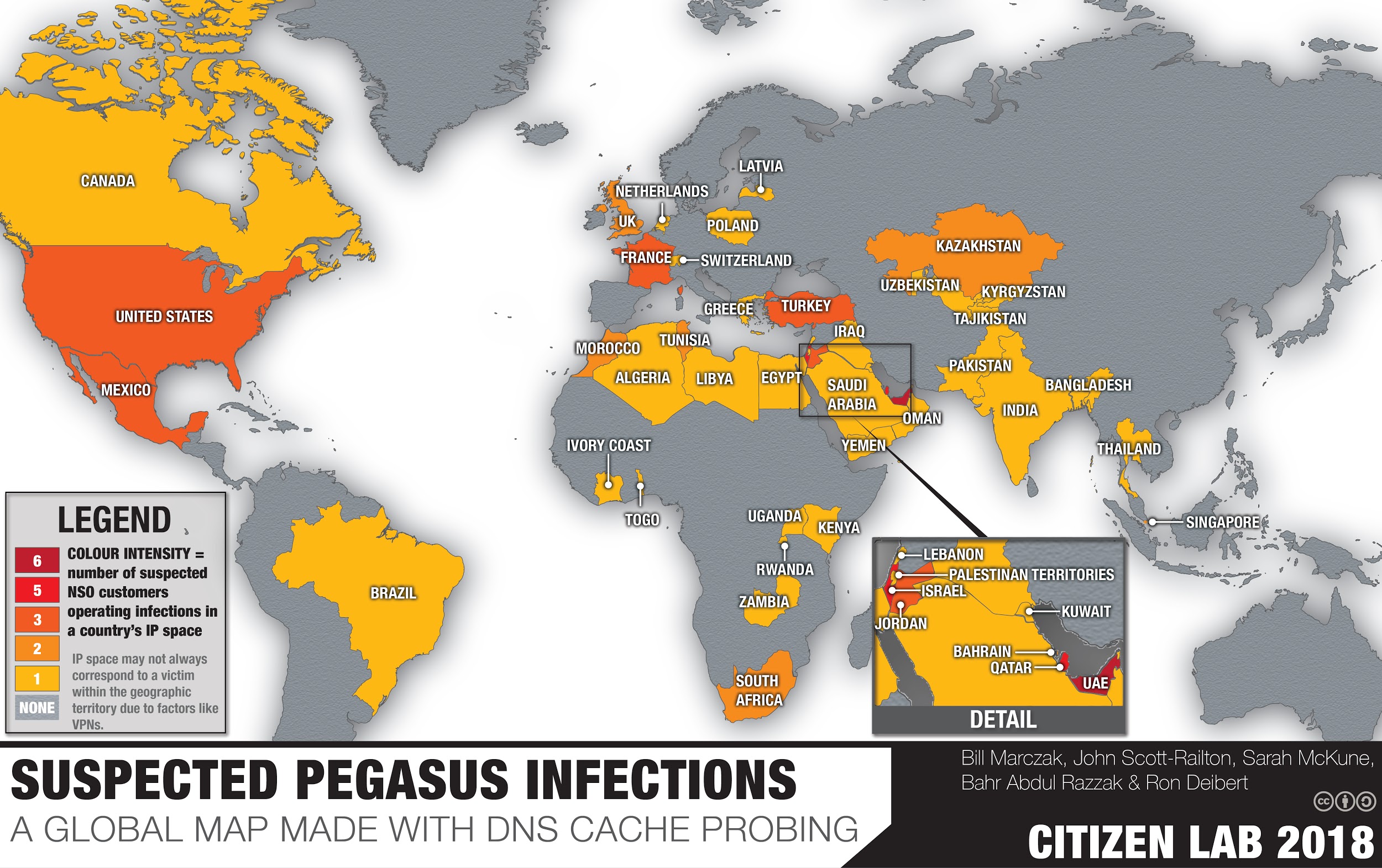 Among the likely government clients are a number with a highly-problematic track record not only of human rights abuses, but also prior abuse of commercial spyware. This list includes:
Among the likely government clients are a number with a highly-problematic track record not only of human rights abuses, but also prior abuse of commercial spyware. This list includes:
- Bahrain — a country Amnesty International recently described as descending into “a full-blown human rights crisis”;
- Kazakhstan — a country with a track record of abusing spyware to target journalists and activists critical of the government;
- Mexico — a country that was the focus of six separate Citizen Lab reports that exposed government surveillance of research scientists, health advocates, journalists, and international investigators into mass disappearances, including four reports that were the subject of separate front page exclusives in the New York Times in 2017;
- Morocco — the subject of a 2012 Citizen Lab report on the use of Italy-based Hacking Team’s spyware to target the Moroccan citizen media and journalism project Mamfakinch;
- Saudi Arabia — a country whose track record Human Rights Watch describes as including “arbitrary arrests, trials, and convictions of peaceful dissidents.”
- The United Arab Emirates — the country in which we first encountered NSO Group in 2016 when we determined that the UAE had employed NSO Group technology to target the iPhone of award-winning human rights defender Ahmed Mansoor. Mansoor is presently serving a 10-year jail sentence for social media posts critical of the government.
The companies that sell commercial spyware claim they “follow local laws” and export control requirements. That claim is certainly true, but also precisely part of the problem. Some government clients use technology developed by companies like NSO Group not just to investigate what most reasonable people would describe as genuine “criminals” or “terrorists”; our research has shown they also use it to monitor the private communications of activists, human rights defenders, journalists, and other members of civil society. For corrupt or autocratic rulers whose aims are to limit human rights and public accountability, those are “legitimate” targets. This is the type of “local law” that companies like NSO Group follow.
Meanwhile, export controls are weak, flawed, or in some cases non existent. As a consequence, there is little disincentive for the companies to control the abuse of their technology. They reap the private rewards while passing the responsibility on to others. Clearly, as our report shows, NSO Group is either unable or unwilling to prevent the abuse of its technology and did not take any noticeable measures to restrict the use of its powerful surveillance technology even after widespread public reporting on cases where their surveillance technology was abused.
On 14 September 2018, I sent a letter on behalf of the Citizen Lab to two NSO Group principals, Mr. Omri Lavrie and Mr. Shalev Hulio, notifying them of the details of this report, explaining that we had shared an embargoed copy with journalists, and offering to publish in full any response they wished to communicate on the record.
NSO Group principals responded with initial emails, and a full public statement, which we are posting in full alongside our report. In part, the statement claims:
“NSO has several times requested a meeting with Citizen Lab so we could present our position and provide additional details on our product. As in the past, Citizen Lab has not responded to our request to meet about this report and published a misleading report.”
I have no record of any such prior requests. More importantly, although I am always willing to listen to and learn from people who are involved in cases that are the subject of our research, I do not believe that a private meeting is a proper substitute for responsible communication on a serious matter of public interest.
The NSO statement also says “NSO Group develops products that are licensed only to legitimate government agencies for the sole purpose of investigating and preventing crime and terror. The company works in full compliance with all applicable laws, including export control laws.” The statement goes on to claim that there is a “Business Ethics Committee” operating at NSO Group “which includes outside experts from various disciplines, including law and foreign relations, [which] reviews and approves each transaction and is authorized to reject agreements or cancel existing agreements where there is a case of improper use.” However, no comment was made or explanation given about the continued, repeated cases of abuse we have identified in spite of the supposed scrutiny of this committee.
What is to be done, then, about the proliferation and abuse of commercial spyware?
Awareness about these issues is still a very important part of the process. To that end, we at Citizen Lab will certainly continue to refine our methods to allow us to better uncover the continued proliferation and abuse of commercial spyware, and we encourage other research groups to use the methods we have developed to do the same.
Litigation of various sorts may also be an option. It is noteworthy that our report discloses that several of the operators using NSO Group technology are engaged in surveillance across international borders. We have no indication whether the country operators undertaking such cross-border surveillance are doing so with the permission or knowledge of the governments in whose jurisdictions they are spying. However, many countries in which such surveillance is occurring — for example, Canada, the United Kingdom, the United States — have laws that prohibit eavesdropping without a warrant. By facilitating and abetting such cross-border surveillance, NSO Group may be exposed to serious legal risks. Indeed, NSO Group is currently the target of two separate lawsuits alleging illegal spying. These legal risks should certainly cause ownership groups and investors to consider their own liabilities as a result of lax controls. NSO Group is currently owned by US-based investment firm, Francisco Partners.
Lastly, there is the prospect of more effective government oversight concerning the export of commercial spyware. Although the Israeli government has claimed it has strong export controls in this area, our research and other reporting shows clearly there are major gaps. It is ultimately up to Israeli policymakers, and Israeli citizens, to determine whether the continued harms caused by the abuse of commercial spyware that we document warrant new and more stringent export controls. We believe they do.